About Portspoof
The Portspoof program primary goal is to enhance your systems security through a set of new camouflage techniques. As a result of applying them your attackers' port scan result will become entirely mangled and to very significant extent meaningless.
Techniques used to achieve this:- All configured TCP ports are always open
Instead of informing an attacker that a particular port is in a CLOSED or FILTERED state a system running Portspoof will return SYN+ACK for every connection attempt.
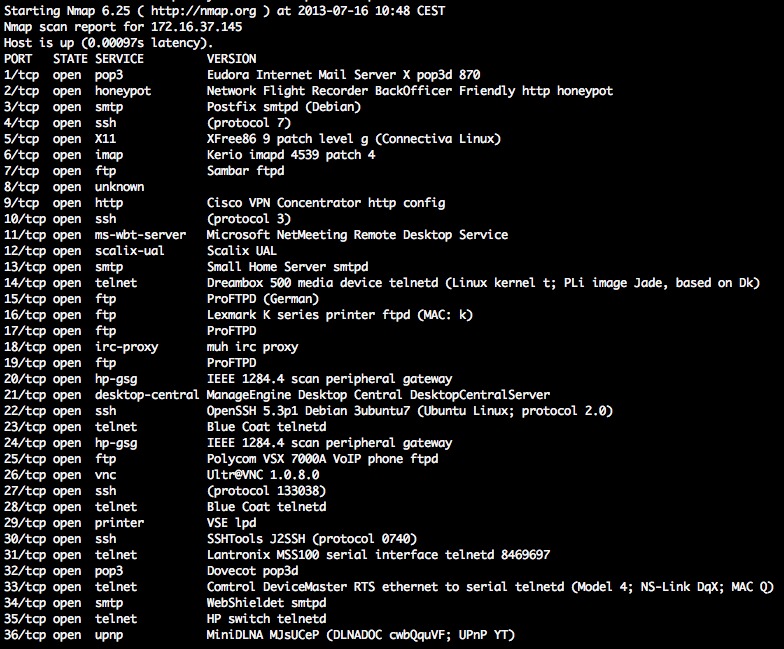
Result: As a result it is impractical to use stealth (SYN, ACK, etc.) port scanning against your system, since all ports are always reported as OPEN. With this approach it is really difficult to determine if a valid software is listening on a particular port (check out the screenshots).
- Every open TCP port emulates a valid services
Portspoof has a huge dynamic service signature database, that will be used to generate responses to your offenders scanning software service probes.
Scanning software usually tries to determine a service that is running on an open port. This step is mandatory if one would want to identify port numbers on which you are running your services on a system behind the Portspoof. For this reason Portspoof will respond to every service probe with a valid service signature, that is dynamically generated based on a service signature regular expression database.
Result: As a result an attacker will not be able to determine which port numbers your system is truly using.
Reverse exploitation with Portspoof:
Portspoof can be used as an 'Exploitation Framework Frontend', that turns your system into responsive and aggressive machine. In practice this usually means exploiting your attackers' tools and exploits.
At the moment there are few example exploits in the configuration file (portspoof.conf). One of them exploits Nmap 6.25 default script.
Overview:
Portspoof is meant to be a lightweight, fast, portable and secure addition to the any firewall system or security system. The general goal of the program is to make the reconessaince phase slow and bothersome for your attackers as much it is only possible. This is quite a change to the standard 5s Nmap scan, that will give a full view of your systems running services.
By using all of the above mentioned techniques together:
- your attackers will have a tough time while trying to identify all of your listening services.
- the only way to determine if a service is emulated is through a protocol probe (imagine probing protocols for 65k open ports!).
- it takes more than 8 hours and 200MB of sent data in order to get all of the service banners for your system ( nmap -sV -p - equivalent).
Videos
Nmap scan against system protected by Portspoof:
Exploiting your attackers automated exploit scripts with Portspoof:
Exploiting your attackers Nmap NSE script with Portspoof:
Features
The most important features that Portspoof has:
- Portspoof is a userland software and does not require root privileges ! - Binds to just one tcp port per a running instance - Easily customizable through your iptables rules - Marginal CPU/memory usage (multithreaded) - More than 9000 dynamic service signatures are supported !
Check out the documentation page for further details.Log
For full log details please visit https://github.com/drk1wi/portspoof
1.1 - 1/01/2014 - Linux * Minor release. * Updated reverse regular expression generation engine (used for generting bogus service signatures). * Over 9000 service signatures in the portspoof_signatures file.. * Better memory management. 1.0 - 02/08/2013 - Linux * Major release. * Ported to C++. * Example NMAP NSE exploit, McAffe UTF7 XSS, etc. exploits added . * Fuzzer functionality added. * Many minor improvements and enhancements have been made 0.3 - 28/09/2012 - Linux * Configuration file support. * Minor bug fixes and improvements. * Droppped BSD support due to time constraints (will resume in future - maybe). * 8000 port signatures supported 0.2 - 11/08/2012 - Linux/BSD Note: BSD implementation is still experimental * Alerts can be logged for further investigation. * Fixed BSD startup bug. * Automake files fixed. * Other minor bugs fixed. 0.1 - 02/08/2012 - Linux/BSD * First stable release for Linux. * Multithreaded. * 1866 port signatures supported.
License
Portspoof is a free software distributed under GNU GPL version 2 license.
All the relevant details can be found here
Support
If you like Portspoof and would like to support this project then please aid me with a cup of coffee :)